Generative AI, or GenAI, changed how businesses operate by automating tasks, enhancing efficienc and providing valuable insights for data-driven decision-making. It enables personalized customer experiences, fosters innovation by automating tasks, and ensures adaptability in dynamic markets. With continuous learning capabilities, GenAI empowers businesses to stay competitive, make informed decisions and evolve smarter, more resilient models.
As businesses rush to embrace the potential of GenAI, a new report from Info-Tech Research Group warns early adopters to proceed with caution. "Address Security and Privacy Risks for Generative AI" highlights the significant risks posed by this nascent technology, including unauthorized use and data security loopholes.
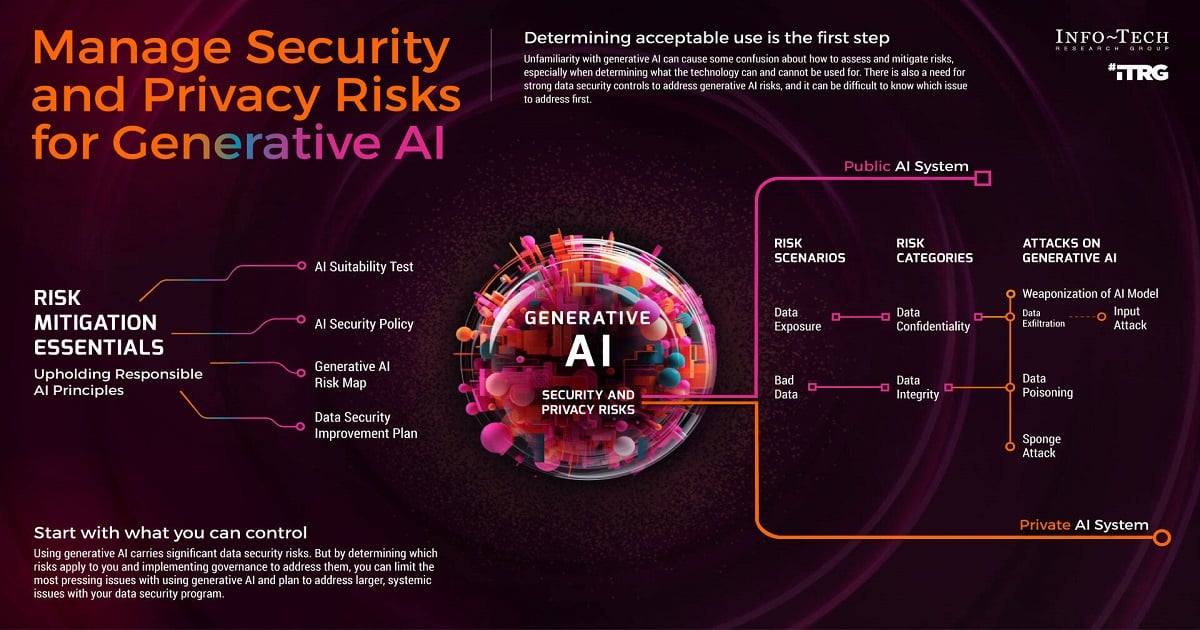
The report emphasizes that the novelty of GenAI poses unique challenges in risk assessment and governance. Unlike established technologies, robust security frameworks haven't yet been developed, leaving organizations vulnerable to data breaches, unauthorized deployments and even AI-generated misinformation.
One key concern identified by the report is the potential for unauthorized use of AI models. In the absence of stringent safeguards, there exists a risk that employees within an organization or external actors could exploit AI tools for nefarious purposes.
This misuse is seen in various forms, ranging from compromising sensitive data to generating harmful content. Without effective mechanisms to restrict and oversee access, the potential for unauthorized manipulation of AI models raises concerns about the integrity and security of the systems in place.
The report also highlighted the importance of data security vulnerabilities. Given that generative AI systems heavily depend on vast datasets to learn and generate content, they inherently become susceptible to potential data breaches and privacy infringements. The very nature of these systems involves processing and analyzing large amounts of sensitive information, ranging from personal details to proprietary data.
Organizations venturing into the adoption of generative AI must prioritize the fortification of their data security infrastructure. This entails implementing robust encryption protocols, access controls, and monitoring mechanisms to safeguard against unauthorized access and potential cyber threats.
“Most risks associated with Gen AI are data-related, meaning that effective AI security depends on existing maturity elsewhere in a security program,” said Logan Rohde, Senior Research Analyst at Info-Tech Research Group. “The good news is that the greatest and most common risks of using Gen AI can be addressed with an acceptable use policy.”
The report delineated a strategic framework for organizations leveraging generative AI. This framework encompasses various components.
Firstly, conducting a comprehensive risk assessment is imperative. This involves a thorough evaluation of potential risks associated with the specific GenAI implementation in use. Secondly, implementing robust data security controls is essential. It is crucial to ensure that the data used to train and run GenAI models is well-protected from unauthorized access and manipulation.
Organizations also need to implement clear usage policies and access controls. Organizations should establish unequivocal guidelines for the authorized use of GenAI tools and limit access to those individuals who genuinely require it.
Moreover, developing effective monitoring and logging procedures is a key aspect. Continuous tracking of GenAI activity is necessary to detect and prevent unauthorized use or misuse. And a final key point is establishing governance structures. Clear oversight mechanisms should be put in place to ensure the responsible and ethical use of GenAI technology within the organization.
GenAI offers substantial opportunities across industries, yet Info-Tech's Exponential IT research indicates that AI security is still evolving. The latest Gen AI blueprint emphasizes the importance of developing specific controls and techniques, recommending organizations to rely on a robust data security program.
Be part of the discussion about the latest trends and developments in the Generative AI space at Generative AI Expo, taking place February 13-15, 2024, in Fort Lauderdale, Florida. Generative AI Expo discusses the evolution of GenAI and feature conversations focused on the potential for GenAI across industries and how the technology is already being used to create new opportunities for businesses to improve operations, enhance customer experiences, and create new growth opportunities.
Edited by
Alex Passett